The Engineering Workplace as a product
•
16 February 2026
•
7 mins
Most companies don’t have an engineering workplace product. They have devices, policies, tooling portals, roles portals, documentation but they don’t have a product. And that distinction is crucial: the environment in which engineers work directly influences on boarding speed, security, engineer experience, and ultimately business velocity. When treating the engineering workplace as a product, everything changes.
Why an engineering workplace?
In general there are a couple of subjects that prevent either software engineers, and related to the same product, security personnel to do their jobs more frictionless:
For engineers, friction often starts on day one:
- On boarding is time-consuming and confusing
- Tools are scattered across different portals
- Documentation is outdated or inconsistent
- It’s unclear which tools are permitted
- Configuration is manual and error-prone
- Laptop replacement feels like starting over
This creates frustration before value creation even begins.
From a security perspective, there are different challenges:
- Ensuring secure configurations
- Preventing untrusted tool installations
- Reducing shadow IT
- Managing risk without blocking productivity
The classic anti-pattern emerges: “One workplace to rule them all” but when engineers are treated like standard office users, companies often end up granting full admin rights just to avoid blocking work. That is not a strategy. It’s bad practice.
The product
An engineering workplace, like any other product for that matter, should help it’s users doing their jobs to be done. It should not be another product where users have to navigate. It also should facilitate innovation rather that restrict it, while making sure it is safe.
Product Vision
The Engineering Workplace enables engineers to create business value from day one: securely, seamlessly, and without distraction. It reduces cognitive load and balances developer experience and security by design, not by compromise, and evolves alongside the way we build software.
Business goals
If the Engineering Workplace is a product, it must have measurable outcomes. Otherwise, it remains infrastructure. You can distinct at least four categories:
Productivity & On boarding Speed
The most visible impact is how quickly engineers become productive.
Core metrics:
- Time to productive environment
- Time to first pull request
- On boarding duration (contract start → first merged PR)
The goal: Reduce setup friction to near zero and enable value creation from day one.
Operational Efficiency
A well-designed workplace reduces internal support overhead.
Indicators:
- Reduction in admin rights requests
- Fewer additional tool approval tickets
- Decrease in workplace related service desk tickets
- Decline of used workarounds (used tools and configurations)
If these numbers decline, the product is working.
Security & Risk Reduction
Security should improve without slowing down development.
Key signals:
- Reduction in usage of unapproved software
- Decrease in unlicensed tools
- Fewer exceptions for local admin privileges
- Decline in usage of unofficial package sources
- Standardized secure configurations across profiles
Security maturity becomes embedded in the system instead of enforced reactively.
Developer Experience (DevEx)
Quantitative data must be complemented by personal perception.
Qualitative measurements:
- DevEx satisfaction rating
- Internal developer surveys
- Community feedback
- Profile adoption rates
If developers bypass the system, the product has failed, regardless of technical correctness.
The Strategic Insight
The most important shift was this:
Stop measuring success in terms of “devices delivered” and start measuring:
- Time to value
- Friction reduction
- Risk reduction
- Adoption
Principles
Treating the Engineering Workplace as a product required explicit design principles. These principles guided decisions, trade-offs, and prioritization.
Provide a better alternative to achieve the desired state.
Instead of blocking behavior and fighting workarounds, focus on providing a better alternative. If the official tooling, package sources, and workflows are easier and faster than unofficial ones, developers will naturally choose them. Security should feel invisible because the right path is also the most convenient one.
Engineers should never need administrative rights to perform their jobs.
If elevated permissions are required, the system design is incomplete. The workplace must provide everything needed without forcing users into risky workarounds.
Developers are not generic office users.
Different engineering roles require different tool stacks, permissions, and configurations. Instead of enforcing one universal setup, use structured profiles. Profiles bundle: tools, access rights, security configurations and permissions. This enables standardization at scale without disturbing the user experience.
From few to many controls
Traditional workplaces operate in extremes: Full control (local admin, unrestricted installs) or Full restriction (locked-down environments). Neither supports modern engineering effectively. The product is designed around fine-grained controls. This creates a deliberate balance between developer experience and security.
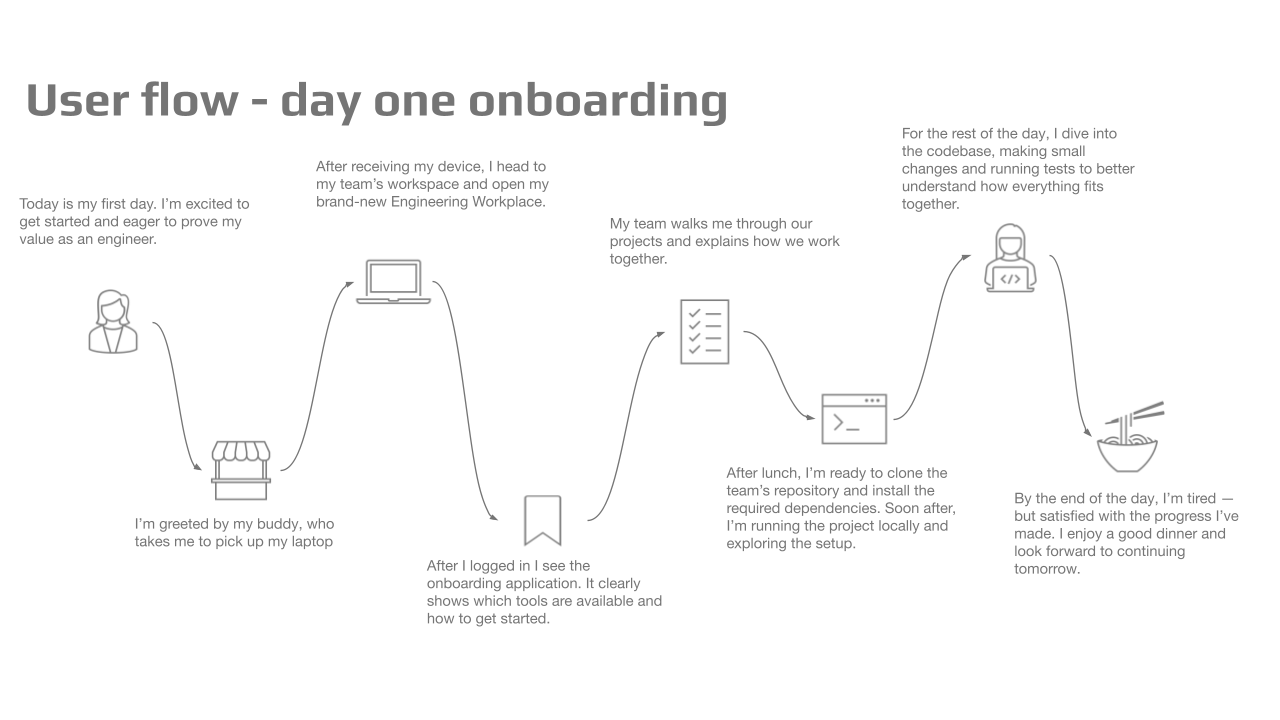
User flows
From day one, the user flows are the most important artefacts. It enforces designing a system that is in essence user focussed. The most important question is ‘how do we make sure our users will focus on business value adding work and not on distraction?’. For the mvp the most important user flow was first day on boarding and device switch.

how
Pattern: Role-Based Engineering Profile
One of the most effective mechanisms for scaling an engineering workplace is profile-driven provisioning. Instead of treating all engineers the same, define structured profiles based on roles and technology stacks.
Start with a generic engineering baseline, including:
- Core access (e.g., source control, cloud platforms)
- Open-source tooling
- Standard IDE
Then layer stack specific profiles that bundle licensed and specialized tools (e.g., enterprise IDEs, design collaboration tools, stack specific SDKs).
Pattern: Pre-Provision Before Day One
Based on the profile and the related tools and their configuration we can already make sure certain policies are deployed on the workplace. For engineers that need Docker or Visual Studio we can deploy certain rules that make it so that they do not need admin rights in order to install, update, install workspaces and use the application. No need for them to request any additional rights. It just works for them!
Provide the workplace with needed:
- Required system policies
- Pre-approved permissions
- Secure installation paths
No additional access requests. No manual configuration. No admin rights. If on boarding starts with ticket requests, the system design is incomplete. Pre-provisioning shifts effort from reactive support to proactive product design.
Pattern: Invisible, Guided On boarding
On boarding should feel effortless and not frustrating and confusing.
Engineers should not need to:
- Search outdated documentation
- Understand internal infrastructure names
- Debug device management policies
- Interpret unclear system errors
Automation should handle everything possible. When user input is required, it must be:
- Minimal
- Contextual
- Non-technical
- Clearly actionable
Pattern: Govern the Supply Chain
Open-source ecosystems are powerful but increasingly targeted. Instead of restricting developers, control the distribution layer.
Examples include:
- Package proxies for Node.Js and Python
- scanning dependencies before installation
- Evaluating package managers (e.g., system-level installers) against security policies
- Managing IDE extensions, browser plugins, and AI tools intentionally
When distribution is governed properly, developers remain productive without bypassing controls.
Pattern: Documentation as Executable Code
If a configuration step can be written down, it should be scripted. Traditional on boarding relies on static documentation which is often outdated and inconsistent. Instead, convert setup knowledge into executable automation.
By using shared inner-source repositories and task runners, engineers should be able to configure environments with a single command including all the company specific configurations and security setup.
This approach:
- Reduces human error
- Ensures consistency
- Turns tribal knowledge into shared infrastructure
- Makes improvements incremental and version controlled
The guiding belief:
If it’s repeatable, it should be automated. If it can be written down it can be scripted.
From control to enablement
Every product, every feature, every platform initiative depends on the environment in which engineers build. If that environment creates friction, everything slows down. If it enables focus, everything accelerates.
Treating the workplace as a product changes the conversation. You stop asking:
- “How do we lock this down?”
- “Why do engineers need all these tools?”
- “How do we support this device?”
And start asking:
- “How do we reduce time to value?”
- “How do we design for adoption?”
- “How do we make the secure path the easiest path?”
When on boarding becomes boring because it just works, when admin rights stop being a discussion, when engineers focus on business problems instead of configuration—then the engineering workplace has become what it should be: A product that enables all other products.
Like it? Share it!